Employees at F.W. Madigan, a Worcester construction contractor, regularly receive suspicious emails from their superiors. The problem is, the emails aren’t really from their bosses and the messages are scams.
Get Instant Access to This Article
Subscribe to Worcester Business Journal and get immediate access to all of our subscriber-only content and much more.
- Critical Central Massachusetts business news updated daily.
- Immediate access to all subscriber-only content on our website.
- Bi-weekly print or digital editions of our award-winning publication.
- Special bonus issues like the WBJ Book of Lists.
- Exclusive ticket prize draws for our in-person events.
Click here to purchase a paywall bypass link for this article.
Employees at F.W. Madigan, a Worcester construction contractor, regularly receive suspicious emails from their superiors.
The problem is, the emails aren’t really from their bosses, and the messages are scams – attempts at tricking an employee into wiring money to someone, giving tax information or buying gift cards on their behalf.
“I’ve had a bunch of them,” said Dennis Serocki, F.W. Madigan’s controller, who handles much of the small company’s information technology matters. “Email – it’s very, very dangerous.”
F.W. Madigan is not alone.

Cybersecurity was once nearly as simple as changing a password every so often, or making it tougher to guess than, say, “password.”
Today, hacking – and those defending against it – is far more complex. Even worries consumers once had about their credit card information being stolen, such as in the well-known case of Target in 2013, are less of a concern.
For a lot of companies, worries have evolved into keeping valued information in the cloud, a more secure location in a tightly guarded data center than in a hard drive in an office ripe for a break-in.
Attacks are increasingly coming in what’s called phishing, when emails look to be from a boss, colleague or even a relative.
These emails may be from a hacker using that person’s actual email address, but more often, a closer inspection will show an unexpected email address that’s actually sending the message behind the familiar name.
Enough workers are falling for the scams they’re creating a major cost.
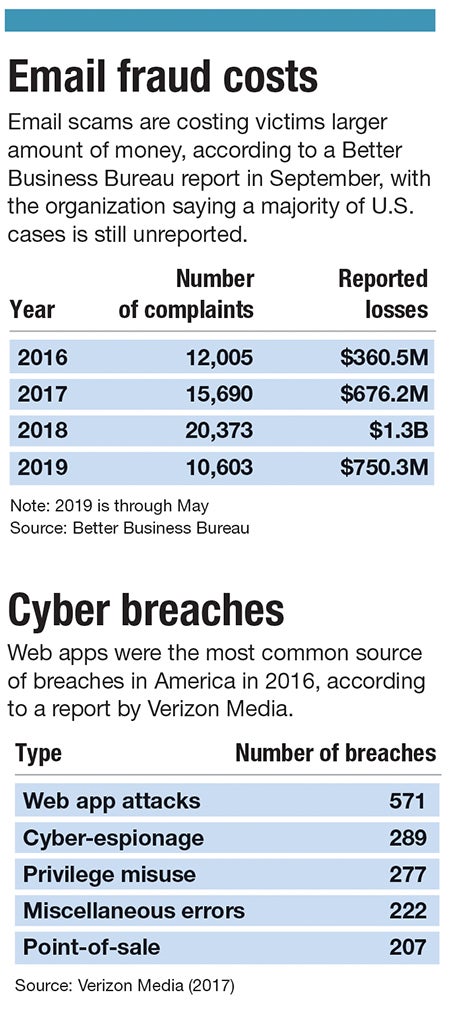
A national Better Business Bureau study released in September showed $3.1 billion in reported losses over less than three and a half years starting in 2016. Last year, those losses totaled $1.3 billion.
The emails almost always give a sense of urgency, the study said, perhaps through subject lines like “urgent/important” or asking, “Are you at your desk?”
Those are the kinds of emails Serocki said he gets roughly weekly – and promptly deletes. He’s taken to reminding workers at staff meetings of the dangers, even giving examples of some fraud attempts aimed at the company.
F.W. Madigan works with an outside IT company and has bought cyber insurance to help in the event of a data breach or hack.
“It’s about implementing controls in your environment, and to make it easy for people to verify information,” Serocki said.
Evolving risks
Passwords still are not changed often enough or made difficult enough for hackers to guess. A major data-breach investigation by Verizon Media in 2017 said weak or stolen passwords were to blame for 80% of hacking-related breaches.
But as cyber technology has changed in recent years, so have risks to users.
Today, smartphone users can download a seemingly never-ending list of free apps, but they’re sure to come with disclaimers requiring permission to allow the app to track the user’s data, or access contacts or even photos. Websites regularly use cookies, tools tracking the browsing activity of users and making possible advertisements popping up on one website shortly after a web search moments earlier.
Cybersecurity and privacy experts recommend steps including researching reviews of apps and not downloading those seeking access to files they don’t need. Web users can choose to use private browsing to keep viewing history from being tracked.
More often, scammers dial phone numbers with what appears to the receiver as a very similar number to their own – a way to try deceiving the person into thinking the caller must be nearby, perhaps a neighbor.
As companies and the security departments or firms they work with have increased their defenses, hackers have changed their methods as well.
“It is an arms race. We do have an ebb and flow going back and forth,” said Craig Shue, a computer science professor at Worcester Polytechnic Institute. “It almost feels like a competitive sport at times.”
Cameron Shilling, a privacy and information security attorney at the New Hampshire law office of McLane Middleton, gives an example how. The well-known customer information breach at Target led to credit card companies installing secure chips scanned in a way that makes data theft nearly impossible, he said.
That makes such attempts not so worthwhile for hackers.
“Credit card theft is just not lucrative,” Shilling said in an October meeting of The Communicators Club, a Central Massachusetts group for media professionals.
Identity theft has become more common, he said, because unlike a credit card, a person can’t simply cancel and obtain a new identity. A hacker might not necessarily need to break into a major bank for vital financial information, he said, but could find a weak spot with a small financial planners’ office, for example.
Municipalities can often be easy targets as well, Shilling said, because they store lots of personal information, aren’t regulated like businesses are, and have very little money to spend on bulking up cyber defenses.
Dozens of cases of municipalities large and small being hacked – and sometimes paying a ransom to get their data and security back – have popped in the last few years. Leominster paid $10,000 in cybersecurity ransom in April 2018 after a cyber attack on its school district.
Regulation & enforcement
Massachusetts has made cybersecurity a higher priority as cyber crime has taken larger financial costs at public entities and businesses.
In April, the Gov. Charlie Baker Administration committed $135 million for a new security operations center for the state’s digital assets, for vulnerability testing of state IT infrastructure and statewide IT systems.
Massachusetts is one of a few states in the nation, Shilling said, to have regulations in place on business cybersecurity, along with California and New York.
The Data Breach Notification Law requires Massachusetts businesses and others owning or licensing personal information of Massachusetts residents to notify the state when they learn of a security breach. They must also notify consumers whose information may have been compromised.
Insurance companies have begun offering cybersecurity coverage, with Worcester’s Hanover Insurance Group the latest to do so, announcing its new service in October.
Enforcing charges against hackers can be more difficult.
Hackers are often overseas, in Eastern European countries, China or North Korea, where they’re far harder for American officials to ever reach, Shilling said. Most fraud cases involve defendants in Nigeria, the Better Business Bureau said in its report.
In September, the Federal Bureau of Investigation said it made 281 arrests in an international business email schemes, recovering roughly $118 million in fraudulent wire transfers. Of those arrests, three-fourths were outside the United States.
Shilling and Shue are both optimistic about protective tools available, but they are cautious about how well businesses, other entities and individuals are keeping themselves safe.
Shue suggests YubiKey, a small device plugging into a laptop’s USB port and, with a tap of a finger or touch against a cellphone, ensures the person logging in is at the location where an account is being accessed.
Shilling recommends protection systems FortiClient, LifeLock or Experian. But no protection can work if a business or person doesn’t take steps to put measures in place, he said. He is adamant many don’t place high enough of a priority on cybersecurity, estimating four out of five don’t put information security measures in place.
“You don’t have to know how to do this,” Shilling said. “You just have to find the right people who know how to do this.”

