In October, two Central Massachusetts companies reported cyber attacks, which broke the record for the largest-ever hacks on healthcare organizations recorded in the state.
Get Instant Access to This Article
Subscribe to Worcester Business Journal and get immediate access to all of our subscriber-only content and much more.
- Critical Central Massachusetts business news updated daily.
- Immediate access to all subscriber-only content on our website.
- Bi-weekly print or digital editions of our award-winning publication.
- Special bonus issues like the WBJ Book of Lists.
- Exclusive ticket prize draws for our in-person events.
Click here to purchase a paywall bypass link for this article.
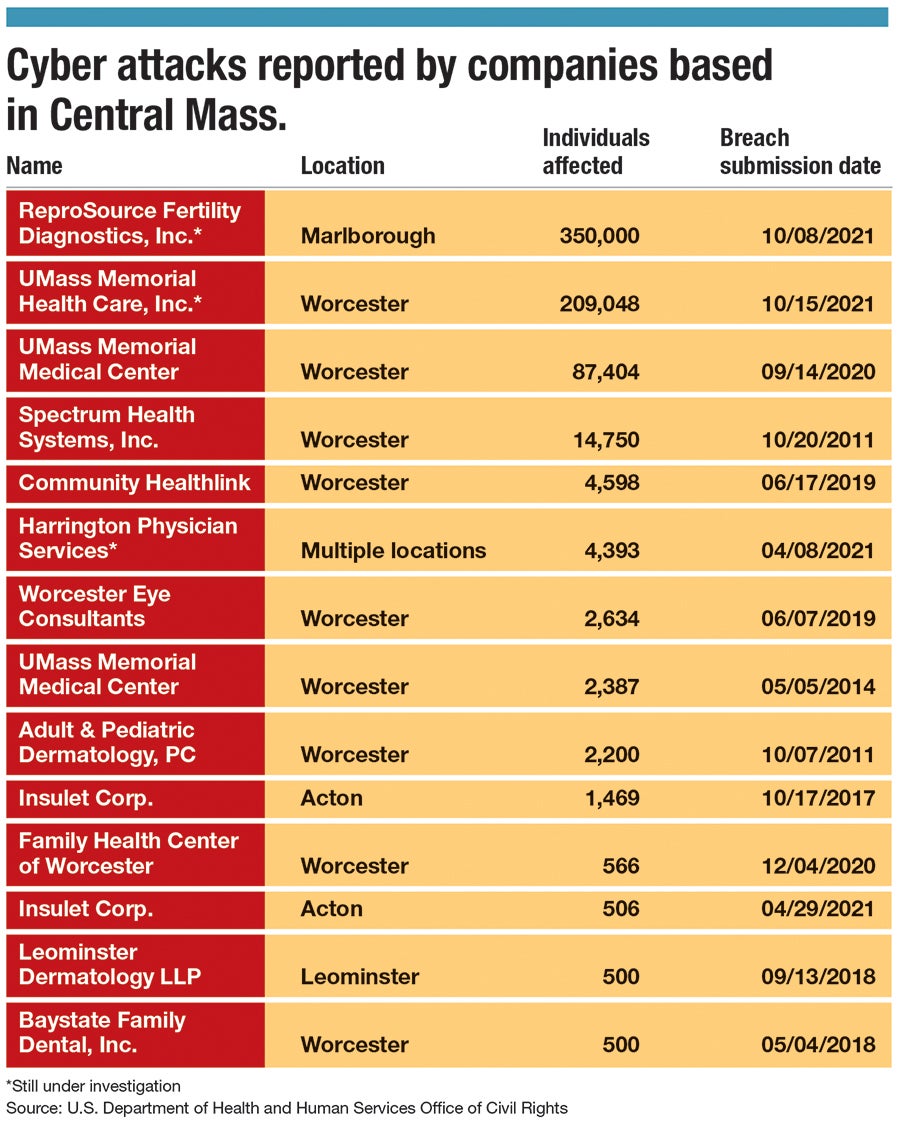
In October, two Central Massachusetts companies reported cyber attacks, which broke the record for the largest-ever hacks on healthcare organizations recorded in the state.
ReproSource, Inc., a fertility clinic in Marlborough, and UMass Memorial Health in Worcester experienced cyber breaches impacting 350,000 and 209,000 patients, respectively. Both organizations discovered the hacks in August and reported them in October, according to their individual releases.
Until then, Massachusetts’ largest cyber attack on a healthcare facility victimized less than 177,000 patients at Lawrence General Hospital, according to reports listed by the U.S. Department of Health and Human Services’ Office for Civil Rights, which tracks these breaches.
The healthcare industry has become an increasingly appealing target to cybercriminals since last year, with Forbes reporting a 42% jump in healthcare breaches in 2020.
As it muddles through workforce and resource shortages, Central Massachusetts health care is facing an unprecedented rise in cyber threats.

A new look for cybercrime
Cybercrime is ever-evolving, said Mike Mosher, director of technology at Worcester-based Cinch I.T., Inc. As businesses build their defenses, hackers adapt to new methods of extorting money and information.
Hackers are “making more money every year. They evolve with the times,” Mosher said. “They’re getting much more sophisticated.”
One of the areas Mosher has seen a huge change is hackers’ abilities to send believable spam emails. Cybercriminals will break into a company’s email account and pick up the internal language of the organization.
“Ten years ago, every spam email was poorly formatted, but we’ve seen with some businesses’ email compromises, they get in and just watch the emails for a couple months,” Mosher said.
Once they understand the lingo, attackers can write a well-veiled spam email asking for sensitive information or requesting a monetary wire transfer. To most employees, the message will appear to authentically come from a higher-up.
At UMass Memorial, hackers had access to employee email accounts between June 2020 and January 2021 for what could have been hours or days, said UMass’s Chief Information Security Officer Bruce Forman. While the attackers didn’t ask for a ransom, they had access to emails with information including insurance data, personal health information, and social security numbers.
Similar information was exposed during ReproSource’s attack on its network system, which lasted less than two days.
Why healthcare is at risk
The financial sector has topped the list as attackers’ favorite, but health care may be giving it a run for its money.
When they’re not directly extorting money through ransomware or wire transfer phishing emails, cybercriminals can sell information to make money.
Personally identifiable information, such as a credit card or social security number, sells for around $1 to $2 on the black market, according to Wisconsin tech and cybersecurity company InfoSec Institute. Meanwhile, personal health information, like medical conditions or insurance settlements, sells for well over $300. Personal health information is more valuable because it can’t be changed the way a credit card can, and criminals can use it to target victims with scams or fake insurance claims.
Along with the appeal of health information, the pandemic has made healthcare organizations more vulnerable, as evidenced by DHHS’s report showing almost every month last year had more than 1 million patients affected by hacks.
The significant uptick in telehealth utilization, as well as more remotely working employees, has made the sector even more reliant on online services. Adding on staffing shortages, which have been particularly acute in the Central Massachusetts healthcare system, businesses are struggling to both prevent and recover from attacks.
“Identifying specifically which patient records were affected and which fields were available is very time consuming, and therefore costly,” Forman said, referring to the nearly seven-month process of determining which patients’ records might have been accessed. UMass hired outside counsel and a forensic firm to help with the process.
Forman said his team was working on introducing multi-factor authentication across the UMass Health system when the hack happened. Multi-factor authentication would have completely blocked the breach, he said, but its implementation into the email system arrived about two weeks late.
“We're looking to hire additional people,” said Forman. “It's tough to find good people. There's definitely a dearth of qualified cybersecurity professionals that are there in the marketplace.”
Forman said it’s a matter of time for health care to catch up on cybersecurity. Multi-factor authentication is now fully implemented at UMass, which he said will be a silver bullet for avoiding similar attacks going forward.
“Health care is probably behind an industry like the financial industry that’s been regulated for a longer time, but it’s catching up,” said Forman.

